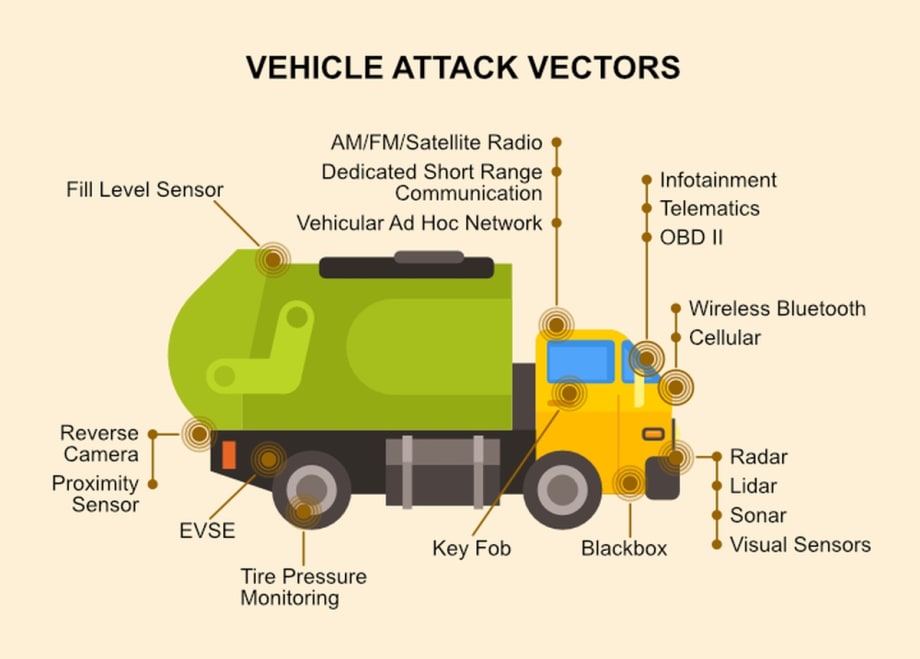
Cars connected to the internet every second can benefit fleets, but this tech comes with a trade-off. For instance, internet connections give hackers openings to attack the vehicle.
In 2015, two computer hackers seized control of a 2014 Jeep Grand Cherokee as a driver ran it through a test range. They did it from their laptops in an apartment miles away. With mere taps on their keyboards, they used the SUV's internet connection to sneak into the vehicle's control access network.
While the truck was in motion, the hackers first toggled the door locks. Next came turning on the windshield wipers. Then they scrambled the dashboard display, rendering it useless. Finally, the programmers disabled the brakes and drove the Jeep into a ditch. The driver couldn't prevent any of it.
Thankfully, the hackers staged the demonstration and didn’t hurt the driver. But they made their point: Threats like this one are real.
Vehicles' Link to the Internet Brings New Cybersecurity Risks
Cars connected to the internet every second can benefit fleets. For example, drivers enjoy following navigation directions on the dashboard. They might like streaming their favorite podcast over the speakers. Likewise, telematics gets more useful when fleet managers see their vehicles' data in real-time.
But this tech comes with a trade-off. For instance, think of a truck constantly linked to the internet in a few different ways. These connections give hackers openings to attack the vehicle from nearly anywhere in the world at any time. It's almost like plugging a bunch of internet cables into the truck — but you can't unplug them or turn them off.
Hackers Can Seize Control of the Vehicle or Steal Data
What kind of cyberattacks are we describing? Let's define two. The first is the vehicle control attack. In this kind of hack, attackers want to control the car — either part or all of it. That Jeep described above is an example.
The motives for this kind of hack can range from mild to deadly. For example, someone might electronically unlock the doors to steal what's inside. But, on the other hand, terrorists might want to harm the driver or those around the vehicle.
The second kind of cyberattack involving a vehicle is a classic data breach. Of course, we all know about data breaches — we read about them in the news all the time. What's new here, however, is that the vehicle is now an avenue for the attack.
For example, many vehicle computers store data about recent routes and driving times, even if the driver isn't using automatic navigation. A hacker who can access the truck's GPS history can steal this data.
Fortunately, we are not aware of these attacks happening in the wild. But unless our industry takes the risk seriously, it’s only a matter of time.
4 Defenses Against Vehicle Cyberattacks
Does all this scare you a bit? Good. Awareness of the problem is the first line of defense. The rest of this article explores strategies you can use to protect your fleet from cyberattacks. We'll start with four general tips.
#1: Place security standards in procurement policies
The first step toward protection is to buy products designed to be secure. So put well-known cybersecurity standards in your purchasing policies and RFPs. If you're unsure which criteria are best, consult your IT folks or an outside specialist.
A good tech vendor should be willing to put security best practices in your contract. Syntech, for example, uses a standard called validated FIPS 140-2 to encrypt every transmission made by our aftermarket telematics devices. So even if a hacker managed to listen to these devices' connections, she couldn't make any sense of the data.
#2: Create and teach a mobile app policy
Whether Android or iPhone, online stores have dozens of apps that connect to your car. Unfortunately, the cybersecurity for these programs ranges from stellar to sad.
Techs using their phones to see trouble codes might sound like a great idea, but an app with poor security can let hackers hop from the phone into the car. A policy and training program can help here. Try identifying a set of handy apps from respected brands, then coach your employees on using just those.
#3: Disable unused capabilities and apps in your vehicles
Unfortunately, the internet connections we've described are often active by default, even when the engine is off. But they don't have to be.
Take Bluetooth as an example. If you have no business purpose for using a truck's Bluetooth service, disable it. Once the connection is off, that's one less avenue for hackers to enter the vehicle's computers.
You can shut down some of these connections via the infotainment system's settings menu. In other cases, you might need to ask the OEM for guidance. Unfortunately, manufacturers don't always advertise how to deactivate these links, but you can do it in most cases.
#4: Deregister vehicles when buying or disposing
De-fleeting a vehicle — or buying a used one — is the perfect time to clean out its digital clutter. Online service providers like OnStar have access to the car's computers and might not know that the vehicle is changing hands.
We know of one fleet operation that purchased a used vehicle but neglected to log the transfer with a built-in online service for unlocking the car. As a result, the prior owner stole back the car after opening it with a mobile app.
So, inform any online service providers tied to the vehicle upon buying or remarketing it.
4 Strategies for Guarding Telematics Data
Telematics is flooding every part of the fleet industry. As a result, this ocean of information is ripe for data theft. Luckily, an aware fleet manager can take precautions. Here are four tactics for guarding your telematics data.
#1: Limit data access to only those employees who need it
The more people who have access to your telematics data, the bigger the risk a hacker will steal it. To counter that risk, grant access to only those who need it.
For example, we have worked with fleet managers who only allow one or two people direct access to the actual telematics data. Those privileged people, in turn, provide summary reports to others.
#2: Facilitate regular updates for telematics devices
We are all familiar with how security patches work for our smartphones. Once in a while, the phone has to download an update with the latest safeguards and restart itself.
The telematics computers on your vehicles do the same thing. These updates happen behind the scenes without needing your techs to do anything — most of the time. But some devices need special conditions for an update to happen. For example, some telematics components don't function when the engine is off. Such devices on an unused vehicle likely aren't getting updated.
Talk with your telematics provider. Understand what your people need to do to make these updates happen.
#3: Anonymize driver data unless you need to identify drivers
There are often good reasons for identifying specific drivers within your telematics data. But such precision presents risks if that data ever makes it into a hacker's hands. Consider GPS history. An attacker who can identify drivers and their location histories knows where and when your specific employees work, park, and take lunch.
Here is a rule of thumb: If you don't need to identify drivers in your telematics, don't. The switch can be as simple as changing a setting in your telematics app.
#4: Clarify who owns the data if you leave your telematics provider
A relationship between a government fleet and its telematics provider isn't permanent. If you choose to switch vendors, understand what the outgoing vendor will do with the data generated from your vehicles.
Why is that important for security? If you have a copy of the information and your old vendor has a copy, there are two copies in the world. That's double the odds that a hacker can steal it. Instead, if your old vendor agrees to delete its copy of your data, then there is only one copy. A good telematics vendor will clarify in your contract what will happen to your information if the relationship ends.